Sacrificing security for usability: UAC security flaw in Windows 7 beta (with proof of concept code)
Sacrificing security for usability: UAC security flaw in Windows 7 beta (with proof of concept code): "
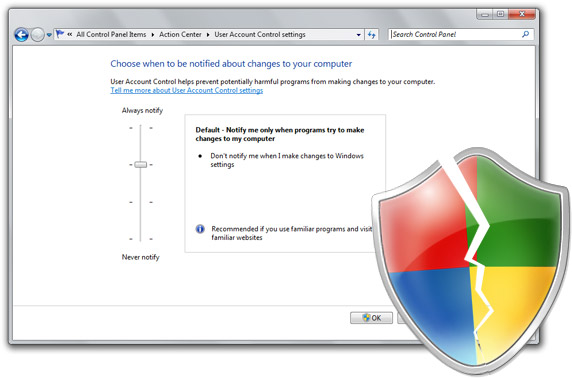
This is dedicated to every ignorant “tech journalist” who cried wolf about UAC in Windows Vista. A change to User Account Control (UAC) in Windows 7 (beta) to make it “less annoying” inadvertently clears the path for a simple but ingenius override that renders UAC disabled without user interaction. For the security conscious, a workaround is also provided at the end. First and foremost, I want to clear up two things.
First, I was originally going to blackmail Microsoft for a large ransom for the details of this flaw, but in these uncertain economic times, their ransom fund has probably been cut back so I’m just going to share this for free.
Secondly, the reason I’m blogging about this flaw is not because of its security implications - it is blatantly simple to fix - but Microsoft’s apparent ignorance towards the matter on their official Windows 7 beta feedback channel by noting the issue as “by design” and hinting it won’t be fixed in the retail version. A security-minded ‘whistleblower’ came forth to ask me if I could publicize this issue to maybe persuade them to change their mind. And that’s what I’m doing.
Now for a bit of background information on the changes to UAC in Windows 7. By default, Windows 7’s UAC setting is set to “Notify me only when programs try to make changes to my computer” and “Don’t notify me when I make changes to Windows settings”. How it distinguishes between a (third party) program and Windows settings is with a security certificate. The applications/applets which manage Windows settings are signed with a special Microsoft Windows 7 certificate. As such, control panel items are signed with this certificate so they don’t prompt UAC if you change any system settings.
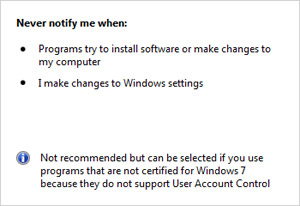 The Achilles’ heel of this system is that changing UAC is also considered a “change to Windows settings”, coupled with the new default UAC security level, would not prompt you if changed. Even to disable UAC entirely.
The Achilles’ heel of this system is that changing UAC is also considered a “change to Windows settings”, coupled with the new default UAC security level, would not prompt you if changed. Even to disable UAC entirely.
Of course it’s not a security vulnerability if you have to coerce the user into disabling UAC themselves (although sweet candy is exceptionally persuasive), I had to think “bad thoughts” to come up with a way to disable UAC without the user’s interaction. The solution was trivial, you could complete the whole process with just keyboard shortcuts so why not make an application that emulates a sequence of keyboard inputs.
With the help of my developer side-kick Rafael Rivera, we came up with a fully functional proof-of-concept in VBScript (would be just as easy in C++ EXE) to do that - emulate a few keyboard inputs - without prompting UAC. You can download and try it out for yourself here, but bear in mind it actually does disable UAC.
We soon realized the implications are even worse than originally thought. You could automate a restart after UAC has been changed, add a program to the user’s startup folder and because UAC is now off, run with full administrative privileges ready to wreak havoc.
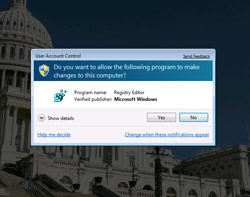 This is the part where one would usually demand a large sum of money but since I’m feeling generous, there is a simple fix to this problem Microsoft can implement without sacrificing any of the benefits the new UAC model provides, and that is to force a UAC prompt in Secure Desktop mode whenever UAC is changed, regardless of its current state. This is not a fool-proof solution (users can still inadvertently click “yes”) but a simple one I would encourage Microsoft to implement seeing how they’re on a tight deadline to ship this.
This is the part where one would usually demand a large sum of money but since I’m feeling generous, there is a simple fix to this problem Microsoft can implement without sacrificing any of the benefits the new UAC model provides, and that is to force a UAC prompt in Secure Desktop mode whenever UAC is changed, regardless of its current state. This is not a fool-proof solution (users can still inadvertently click “yes”) but a simple one I would encourage Microsoft to implement seeing how they’re on a tight deadline to ship this.
Having UAC on at the policy as it is currently implemented in Windows 7 is as good as not having it on at all.
Until when Microsoft decides to fix this, if they do at all, beta users of Windows 7 can also apply a simple fix. Changing the UAC policy to “Always Notify” will force Windows 7 to notify you even if UAC settings change. Annoying, but safe.
Update: I must credit Aubrey from WindowsConnected.com for also touching on this issue briefly today.
Update 2: Microsoft has officially responded to my concerns and continues to insist the functionality is “by design”, dismisses the security concerns and again leans towards they will not be addressing the issue for the final release of Windows 7.
Update 3: A reader has kindly asked me to highlight a particular condition for this to work, the user must be in the “Administrative” user group, and not in the “Standard” user group where they will be prompted for a administrative password. In defense of the seriousness of the issue, the Vista and Windows 7 default user group is “Administrative” and I’m sure that’s what most home users are running.
Update 4: Microsoft’s Jon DeVaan has posted a response on the official Windows 7 blog with an extensive look at the UAC system in Windows 7 and their decision on the default security policy. In conclusion, they continue to stand by their decision and does not indicate they will change the default UAC policy.





















